water damage to a hard drive.
Water damage to a hard drive can occur from a variety of situations:
- flooding, storms, hurricanes
- accidental dropping into water or pool
- extinguishing fire with water
- accidental fluid spills over laptops
- external hard drives accidentally being put into washing machines
Water and electronics don’t mix and hard drives are no exception. In most cases when you experience water damage, you would be throwing ruined electronics out.
But what about the water damaged drive from your desktop computer, laptop, or server which contains critical business data, research or your invaluable, irreplaceable memories?
While you can go to the store and buy a new hard drive, there’s nowhere you can go to buy all of the data you didn’t back up.
how to handle a water damaged hard drive.
It is very important to keep a level head.
act quickly.
Time is important and acting fast is critical. If you have a water damaged hard drive, it’s crucial to understand that media damage will become more extensive over time. Hard drives have a number of electronic components that degrade and corrode when exposed to contamination, and because water is rarely sterile, hard drive damage quickly worsens in the days and weeks following the initial water damage.
cut the power.
Immediately cut the power to your water damaged drive, laptop or PC. This will prevent short circuits that could cause additional damage to the drive. If the damaged device is a laptop, remove the battery.
don't attempt to plug in the hard drive.
In case of water damage, it’s strongly advised not to turn on your laptop, PC, external hard disk, or the server.
It sure feels tempting to plug in and turn it on to see if your hard drive still works. However, plugging in a water damaged hard drive could cause further damage to the drive.
If a water damaged hard drive is turned on, the water on the platters could cause the heads of the disks to rip off, leaving you without the ability to read the information stored on the drive and your data might be lost forever.
If there is still moisture in the circuit board, you could cause a short circuit.
Plugging a shorted hard drive into your computer can also cause further damage to other parts of the computer, such as the motherboard or power supply unit.
don't try to dry out the hard drive.
Don't leave the hard drive to air-dry out on its own. Time is not on your side. The more you let your water-damaged drive sit, the more you risk both internal and external corrosion.
Also, don't dry out the wet hard drive with a hair dryer or any method involving heat - excessive heat can damage the drive even further.
Leave it as is. If the water is contaminated with any particles, they could adhere to the drive's platters and heads. If you dry the water out, this could leave behind residue which makes data recovery more difficult or even impossible.
Data recovery experts know the techniques of carefully cleaning and drying the platters.
don't clean the hard drive.
Remove your drive from the water and dry it off with a clean towel. However, don’t attempt to rinse or clean the hard drive if it is dirty, as doing so without the proper tools almost always makes the situation worse.
don't open the hard drive.
It might seem reasonable to open your hard drive to remove the water inside the hard drive. Don’t do this, because you can expose it to airborne contaminants, dust and particles that can then stick to the platters. This can significantly reduce the chances of a successful data recovery.
pack the hard drive in a sealed bag.
Pack the drive in a moisture-free environment; a plastic sandwich bag or a Ziplock bag are ideal. Try to remove as much air as possible from the bag so that there is less oxygen to react with the hard drive -the presence of oxygen can cause corrosion.
don't try to fix it yourself.
When you see your hard drive wet, you might start to panic. What if you lose your valuable data? How much will it cost to fix this?
You might be tempted to try to fix it yourself to save money or to get it done faster. Or maybe you have a friend or cousin who is handy with computers.
Unless you have professional training, experience, and equipment for dealing with water damaged hard drives, you risk causing more harm than good. First attempt at data recovery is critical. If you make the problem worse, it could take more time, cost more money, or even cause the data to become unrecoverable.
check for backups.
If you have your data stored on other external hard drives, USB drives, or through a data backup service, try accessing any backed up versions of your files to see if and what exactly you have stored.
give the drive to a data recovery specialist.
You should do a little research before you submit your water damaged drive to data recovery. Not every computer repair store has the equipment and knowledge to handle data recovery, let alone the knowledge and skills to perform data recovery from water damaged drives. For optimal results, bring a water damaged drive to a professional data recovery specialist.
check with your insurance company.
If you have data recovery coverage in your small business or homeowner’s policies, this could save you quite a bit of money.
can data be recovered from a water damaged drive.
Most likely yes, if you act fast and follow the above instructions for handling a water damaged drive.
Water often causes extensive damage to both the mechanical and electronic components of hard drives.
When a hard drive gets wet, water can damage a hard drive’s electronics and potentially cause a short circuit. While water can damage a hard drive’s electronics, the data itself is stored magnetically on the platters and will remain there which is why professionals can still recover information from a water damaged hard drive. However, due to damage to mechanical parts of the hard drive, the data may become more difficult or perhaps impossible to recover. This is because the disks of hard drives have tiny, fine heads that read the information stored on the platters. When the water dries, it can leave a film or residue over the platters’ heads. In addition, platters begin to degrade over time due to corrosion, making it much harder to recover data.
Therefore, if you want to get your data back, you should immediately take a water damaged hard drive to a professional data recovery specialist - if possible, within 24 hours. A professional data recovery company will have the tools and facilities to ensure the best chance of a successful data recovery.
how to protect yourself from losing data because of water damage.
Hard drive water damage is a problem that can easily become a nightmare.
Even if you are careful to never eat or drink around your computer, there’s always a chance you’ll get caught in the rain with your laptop or your home/office will flood. There’s no guaranteed way to avoid ever damaging your hard drive.
But there is a way to protect yourself from data loss. Regularly back up your data, both at home and at work - physically, such as on an external hard drive, or digitally in the cloud.
Don’t wait until an accident happens and it is too late. Find a data backup method that works for you and start a daily routine for backing up your data.
If you have a water-damaged hard drive or any other storage device, Kotar Data Recovery can help you get your valuable data back. In order to perform successful data recovery from devices that have suffered severe water damage, we utilize special knowledge and techniques along with extensive experience in the field.
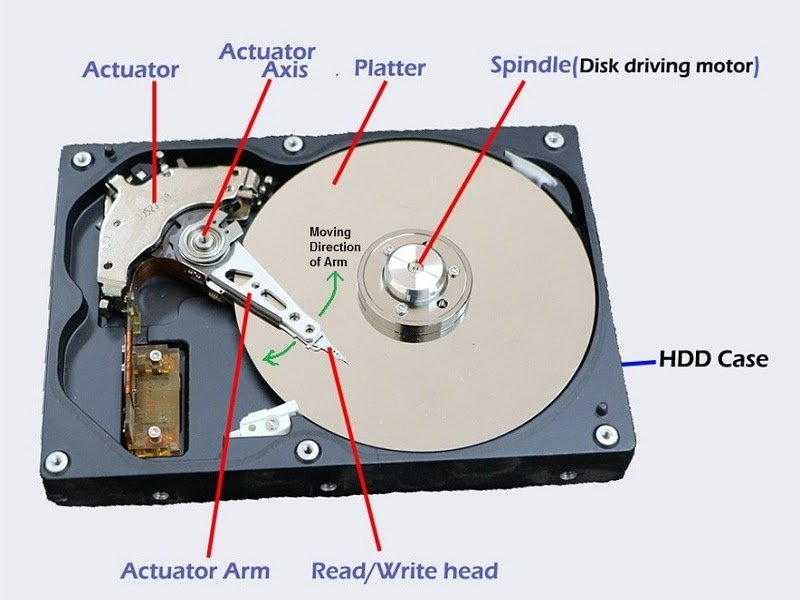
parts of a hard drive.
hard disk drive.
A hard disk drive is an electro-mechanical data storage device that stores data on spinning platters, coated with a magnetic material. The platters are paired with magnetic read/write heads on a moving actuator arm that reads data from and writes data to the platters’ surfaces. Data is accessed in a random access manner. This means that individual blocks of data can be stored and retrieved in any order.
To simplify, imagine that a hard disk is a set of stacked disks, like phonograph records. Each disk has data recorded electromagnetically in concentric circles, or tracks, on the disk. A head, similar to a phonograph arm, writes or reads the information on the tracks. Two heads, one on each side of the disk, read or write the data as the disk spins.
Hard disks come with a rotation speed from 5,400 rpm to 15,000 rpm.
Revolutions per minute (rpm) is a measurement of how many times the disk spins every minute.
Most laptop and desktop PCs use hard disks that fall between 5,400 rpm and 7,200 rpm, while hard disks at higher rpm can be found in high-end workstations and enterprise servers. Disk access time is measured in milliseconds.
The two most common forms of modern HDDs are 3.5-inch, for desktop computers, and 2.5-inch, primarily for laptops.
Hard drives can be external or internal.
They are connected to systems by standard interface cables such as PATA (Parallel ATA), SATA (Serial ATA), USB or SAS (Serial Attached SCSI) cables.
parts of a hard disk drive.
A typical HDD has several disks, read/write heads, a spindle motor that spins the disks, an actuator that positions the read/write head assembly across the spinning disks and a small amount of circuitry, all sealed in a metal case to protect the disks from dust.
disk platters.
A hard disk's platters are the circular, thin metal disks where data is stored. There are typically between 1 and 5 platters stacked on a central spindle with data being stored on both sides of each disk. They spin under the power of the drive spindle motor. Platters are made either out of aluminum, glass or ceramic. They are coated in a number of layers of different materials. The most important is a magnetic layer which is only a few millionths of an inch thick. This layer is a covering of tiny magnetic grains which form microscopic areas that can be magnetized to represent 1 or demagnetized to represent 0. 1s and 0s are then translated into the information that you interact with when you use your computer: the computer’s operating system, software and all other data.
A super thin protective layer above the magnetic media guards against accidental damage and contamination by dust or other material.
the spindle.
Platters are mounted on top of each other on a central spindle. The spindle keeps the platters at a fixed distance apart from each other with enough space for the read/write arms to get to the data on the disks. The spindle is rotated by a spindle motor. The spindle speed is measured in rotations per minute (rpm) and determines how fast data can be written to and read from the hard disk.
actuator arm.
The read and write arm, also called the actuator arm, is the part of the hard drive that reads data already stored on the platter and writes new data on the platter. The read/write arm controls the movement of the read/write heads and makes sure that the heads are in the right position based on the data that needs to be accessed or written. If there are multiple platters in the hard drive assembly, then there will be multiple arms that work simultaneously to read and write data on both sides of each disk platter surface.
actuator.
The actuator unit is a small motor that takes instructions from the drive's circuit board to control the movement of the read/write arm and supervise the transfer of data to and from the platters. It controls the positioning of the actuator arm relative to the disk platter to ensure that the read/write heads are in exactly the right place at all times. This is achieved by an electromagnet assembly, using electromagnetic attraction and repulsion to move the read/write arm in a rapid, smooth, and precise movement.
read/write heads.
As the read/write heads move across the surface of the platter, they read the magnetic surface layer of the disk and convert it into an electrical current which can then be interpreted by software in the computer. Writing data is the opposite, where an electric current is used to change the magnetic field on the required areas of the disk.
There is typically one read/write head for every platter side.
The read/write heads never touch the surface of the disk as this would cause physical damage and make the data unreadable. They float at around 3-6nm (nanometers) above the disk surface and glide over a cushion of air.
When the device is switched off, the read/write arm moves the heads to a parked area away from the disk surface. This prevents the heads from contacting the disk surface in the event of an impact.
circuit board or PCB.
PCB is the green board on the bottom of the hard disk. It allows electricity to pass between various components, controls the functionality of the drive, and allows communication between the drive and the device it is connected to. Like the nervous system of the drive, the PCB contains microcontrollers and other electronics that control the moving arm, the spinning disk motors and the data processing activity.
other components.
Hard disks have other components that aren't central to the physical process of storing and accessing data. These include the data connector, power connector, case, and air filter.
connectors.
Connectors on the PCB allow the hard drive to be attached to a controlling device (PC, Laptop).
Every hard disk has two connectors, one for the power cable and the other for the data cable:
the power connector connects the PCB with the computer's power supply.
the data connector connects the hard drive with a computer's motherboard and it is used for data requests from the hard drive.
Connectors are either IDE, SCSI, USB or SATA. The majority of modern hard drives use SATA connectors.
case.
A hard disk's case protects the contents from dust, dirt and airborne particulate matter, as well as holds all of the components in place.
air filter.
In order for the heads to float correctly over the surface of the platter, the air pressure inside the casing needs to be equal to the air pressure outside of the casing. To achieve this, there is a small air inlet vent which is covered by a filter to prevent tiny particles entering the casing and potentially getting onto the disk surface.
Some drives are actually vacuum sealed. These drives use helium to create the necessary space between the read/write heads and platters. The helium gas limits the chances of read/write head crashes, and since the drives are sealed, there’s little to no chance of media contamination.
what does a hard drive do.
Basically, a hard drive stores digital content or data: documents, pictures, music, videos, programs, application preferences, and operating system.
Everything stored on a hard drive is measured in terms of its file size: megabytes (MB), gigabytes (GB), and terabytes (TB). Documents (text) are generally very small while pictures are large, music is even larger, and videos are the largest.
A hard drive stores binary data through tiny microscopic magnetic lines drawn on a metal disk.
As we mentioned before, a hard disk drive is composed of a spinning metal disk called a platter which is coated with a magnetic material. A read/write head has a powerful electromagnet on its tip which is capable of drawing tiny magnetically charged lines on the surface of the platter. If a line is magnetically attractive it is considered a “0”, if it is magnetically repulsive, it is considered a “1”.
A color rendered image showing the magnetic lines on an HDD platter. The width of the photo is about 1/10 the width of a human hair.
Every desktop computer or laptop has a drive that stores all of the important data. Unfortunately, they can be at risk of data loss due to hardware failures, physical damage, and malware.
Kotar Data Recovery has a long history of expertise with HDD data recovery. We have developed proprietary tools and techniques for recovering data from any make, model, or brand of HDD.
hybrid work and data protection.
Hybrid work environments support a mix of at-home and in-office arrangements.
While the shift to remote work may have felt sudden last year, the pandemic only accelerated what was already a natural progression toward hybrid work. As a result, people are now creating, storing, and sharing data in new ways.
At its most basic level, hybrid work must include both a hybrid workforce and a hybrid technology environment that can support work from anywhere.
unique challenges of hybrid work.
Along with the opportunities, embracing a hybrid work model also presents several challenges.
security
The first potential issue could be that a hybrid workplace makes security a moving target. With employees requiring remote access to the company network on a broad array of devices and from every imaginable location, there is no practical way to set up a security perimeter.
We are talking about a workforce that has spent the last year discovering new ways to work. They are now more mobile, jumping between devices and networks, and also more likely to leverage cloud collaboration technologies to share potentially sensitive information between colleagues. Users are mixing personal and corporate data more than ever, and they are more susceptible to phishing attacks.
Last year, data security threats saw a sharp rise with the introduction of work from home for the majority of companies. This rise happened not only due to malicious outsiders looking to exploit security vulnerabilities, but also due to insider threats such as human error and social engineering.
IT also loses visibility when users are working from home and now has to protect both in-house and remote work environments and allow employees to move fluidly between them. This requires two robust security strategies which must seamlessly work together, whether employees are in the office, in a coffee shop, or in a car.
All of this creates new cybersecurity and data protection challenges for businesses as they transition to hybrid work.
Therefore, for employers, securing their data is one of the most challenging components of managing both in-person and remote workers.
network access and speed
Another big challenge for companies is managing workers logging in to company devices from various locales. The vulnerabilities are increasing as companies expand out that network and more people are working from home.
It is recommended to use a virtual private network (VPN) when accessing your company’s network remotely. A VPN provides an encrypted communication channel between the employee’s device and the server to which it is connecting too. Along with that, a multi-factor authentication (MFA) should always be used where possible. MFA provides a more robust authentication process as it requires additional factors.
Speed could also be an issue. Remote workers are no longer sending requests directly over the internet. A traditional VPN solution means that all those employees are first sending the request to the office network and then the request goes out to the internet. If the VPN connection introduces latency, the delays may disrupt business processes. This can also cause an issue when workers have bandwidth limits in their home locations.
Companies that adopt a hybrid working model should be planning and working towards a truly distributed workforce, with services available securely from anywhere, at any time, and on any device.
endpoint breaches
Because remote and hybrid workers use multiple devices for work and connect with unmanaged devices which raise the potential for data leakage, another great concern are endpoint breaches. While most IT-managed devices download and install security patches automatically when connected to the company network, that's not necessarily happening when someone is working remotely.
disruption
Last but not the smallest challenge of a hybrid workforce is that the disruption of established processes, like productivity, communication and collaboration, will continue.
how to handle hybrid work.
There are key security recommendations for any business looking to adopt hybrid work arrangements for their employees that can help keep their business safe.
dedicate a security team
Companies adopting a hybrid work model should hire or assign IT staff members to focus solely on security or find a managed IT services partner to handle security for the company.
enforce device security
IT should pay special attention to their employees’ devices for work-related tasks. These work devices should be kept up to date with the latest anti-virus and anti-malware software in order to reduce the risk of outsider threats.
For risks originating within the organization, a company should implement a data loss prevention (DLP) solution. With a DLP, a business can minimize the risk of data loss, leakage, and theft by safeguarding sensitive data categories directly. When applied on the endpoint, DLP policies stay active regardless of a device’s location and can, thus, support remote compliance.
Another critical security requirement is securing mobile and printer devices that employees use outside the office wall. Otherwise, companies' data is open to security threats such as phishing, mobile malware, and accidental or intentional data leaks by staff.
To avoid these, companies could establish a bring-your-own-device (BYOD) policy. This should provide clear guidance on what personal devices employees can use for work, how they should access information safely and securely, and best practices for mobile security.
Using appropriate encryption is another essential security measure with a hybrid workforce. Encryption is useful against cyberattacks and cases when a device is lost or stolen, as unauthorized people can’t access the data.
optimize productivity and collaboration
In a hybrid workspace, it is crucial for a company to balance collaboration security and employee productivity.
For remote workers and hybrid teams, collaboration tools are easy to adopt and help to enhance productivity. Still, they also increase security threats through easy and often uncontrolled file-sharing and team collaboration. These tools usually have basic built-in security capabilities but often do not provide adequate protection from some of the most common security risks, like data leaks and data loss.
Insider threats are very present when a team uses work-stream collaboration tools. These can take different forms, such as an accidental share of a customer database, an intentional disclosure of company business plans, or sending sensitive data to the public cloud.
IT must find solutions to reduce these security risks by monitoring and blocking confidential data being shared.
embrace zero trust
“Never trust, always verify” is the core principle of the Zero Trust security model. It means that there is no implicit trust granted to networks, systems, or data. The model assumes that each request to access assets or resources needs verification, whether it comes from inside or outside of the traditional firewall.
If an organization adopts a hybrid model, that means a mobile workforce - it needs to protect people, devices, apps, and data, regardless of their location. Insider threats continue to be a significant risk in this case, and having a zero-trust mindset is helpful whether employees are in the office or work from home.
Another principle of Zero Trust is the least privilege access, which means minimizing each user’s exposure to sensitive parts of the network. Access to systems and applications works on a need-to-know basis, including employees, partners, and contractors.
Micro-segmentation is also a crucial component. This means breaking up security perimeters into small zones to maintain separate access for separate parts of the network.
Multi-factor authentication is a core value of Zero Trust. It requires more than one piece of evidence to authenticate a user: entering a password alone is insufficient for gaining access.
secure cloud-based solutions and services
In hybrid work environments, cloud solutions and services are frequently used because they offer flexibility, accessibility, and easier scalability. Companies can mistakenly believe that the provider is solely responsible for the security of the cloud environment. However, businesses also have a responsibility for securing their data and user access, whether the cloud service is Infrastructure-as-a-Service (IaaS), Platform-as-a-Service (PaaS), Desktop-as-a-Service (DaaS), or Software-as-a-Service (SaaS).
Some of the best practices to secure your information in cloud environments are monitoring, controlling, and limiting access to files, keeping your network security up-to-date, and using strong passwords. It is also recommended to encrypt sensitive data before transferring it to the cloud.
train the workforce
A new working model comes with new threats and demands advanced awareness. This means that security efforts are incomplete without employee training.
If a company wants to remain safe and as efficient as possible in a flexible work environment, it should consider (re)training employees, especially those that are hybrid or fully remote. Focus should be on the threats and risks they need to be aware of, as well as the cybersecurity best practices they need to know.
The hybrid workforce is among the most prominent changes arising in the post-pandemic world. Therefore, securing data across a hybrid IT infrastructure is a primary responsibility for any organization, especially with emerging data protection regulations.
update business continuity and disaster recovery plans
As businesses navigate what comes next, IT professionals must adapt to the changing face of the workplace and create data protection strategies that are up to the challenge.
If a company is moving to a hybrid work environment, it is critical to review the business continuity and disaster recovery plans and update them immediately. An outdated business continuity plan could mean a disaster if a cyberattack, weather event or other unplanned disruption knocks out your systems. The financial cost of rebuilding after a disaster can be overwhelming. If a company is prepared for emergencies, you’ll be in a better position to recover and continue operations in case a disaster strikes.
The world of work is changing and the hybrid working model is becoming the future of work.
This past year has led to an evolution in not only how we think about work, but more importantly, where we get our work done. With the hybrid work model, the amount of data at risk is skyrocketing. In response, companies must take action to strategically measure the viability and effectiveness of their existing security controls and obtain the right level of visibility and control across all devices. By embracing defensive best practices, every business can eliminate blind spots, identify weaknesses, quickly mitigate threats, and significantly reduce the risk of the hybrid working model.
Should data loss occur and your business is in need of recovering critical data, Kotar Data Recovery can help to recover lost data from any situation and any storage device.
data recovery from devices caught in fire.
Summer is the hottest season that, unfortunately, brings a greater risk of fires.
Different types of fires can cause different levels of damage on devices caught in the fire with different possibilities for data recovery.
isolated home/building fire vs. wildfire.
There is a difference between an isolated home/building fire and a wildfire.
Wildfires burn longer and at higher temperatures than an isolated home/building fire.
In the case of an isolated home/building fire, firefighters are usually on the scene in a few minutes and can contain the flame before the fire spreads throughout the entire house. Items caught directly in the flame experience far greater temperatures and suffer greater damage then items elsewhere in the house/building.
On the other hand, homes/buildings caught in a wildfire usually burn continuously for many hours until there is nothing left to burn. The length of fire matters because the longer a flame burns, the hotter it gets. Wildfires burn for long periods of time at extreme temperatures before reaching a home/building, and can thus instantly ignite the entire structure.
Along with the length and temperature, water, soot, and fire extinguishing agents used by firefighters on isolated home/building fires can also cause additional damage to devices. In a wildfire, houses in the middle of the fire simply burn out before firefighters are able to get to them and use water or flame retardant on the fire.
fire damage to different parts of devices.
Devices caught in a fire are not instantly and entirely destroyed. Different parts experience different damage.
1. plastic parts
Plastic components will melt in any fire, whether directly contacted with the flame, or affected indirectly by the heat of a fire.
2. rubber seals
Hard disk drives and solid state hard drives have metal casings that are sealed with an industrial strength rubber gasket. As long as the rubber remains in place, even if softened, the components inside that store data will be protected from external debris. However, once the rubber gasket is compromised and there are holes in the seal, soot, smoke, or other contaminants inside the drive can cause damage to the platters of the hard drive where the data is stored and therefore make data recovery almost imposible.
SSDs are different from HDDs in that the chips that SSDs are made of are not affected by particulates. If an SSD case is compromised, there may still be a chance of recovering the data.
3. platters
Inside an HDD are platters that look like round mirrors on a spindle. All of the computer’s data is stored there. They can be made of aluminium, glass, ceramic, cobalt, or a combination of these materials. Platters are quite durable to heat and can often withstand high temperatures before they begin to warp, bubble, or melt.
4. metal
Computers are generally composed of various types of metals: the exterior case is usually made of aluminium, while the controller chips, memory chips and circuits are usually made of silicon. Other components are made out of lead, copper, gold, or tin.
Silicon is very resistant to heat and can survive very high temperatures. However, even at lower temperatures, durability of silicon and most other metals breaks down with long exposure to heat or flames, and the chances for data to survive on storage devices decrease with each passing minute.
is data recovery from a burned hard drive possible.
Data recovery from a burned drive is possible, however a fire recovery is one of the most difficult recoveries.
There are several factors that determine whether the data may be recoverable from a fire damaged drive.
1. water
Homes and offices are equipped with fire sprinklers that go off in the case of smoke or high temperatures in the room. The water from a sprinkler may be enough to cool the device and prevent permanent data loss. However, once the firefighters start rescuing a burning building, they soak it with a huge amount of water. Even if there were no sprinklers in the building, this large amount of water can damage your devices. Therefore, a device caught in a fire will usually have water damage to it as well. The filter on a drive has filtration for dust particles and some drives have silica gel which reduces moisture in the drive. But even these can not prevent the amount of water damage from a fire hose. In this case, data recovery has to start immediately, before water contamination can start causing corrosion.
2. melting
If the computer is melted and there is no evidence of direct contact with flame (char), data can probably still be recovered. Fortunately, the hard drive is usually buried inside a computer and gets some added protection from there, at the expense of the computer getting ruined. If the hard drive was powered on during the fire, there could be stuck mechanical parts internally. The heat could cause damage to the magnetic coating of the discs which reduces the chances of the platter’s readability. Further on, the heat can cause the discs, which are normally mirror-smooth, to bubble or warp, crashing the heads which causes permanent damage to the platters. In that case, data recovery would be impossible.
3. stickers
If there are still manufacturer stickers on internal components of your computer or your hard drive, this is a sign that the heat was not strong enough to cause permanent data loss and data can most likely still be recovered.
4. case condition
Even if the computer exterior is melted or charred, what really matters is the condition of the hard drive. When the hard drive is still in one piece and the rubber seal that holds the case together is not compromised, data can probably still be recovered.
In most cases, the external electronic parts of the hard drive (PCB) screwed to the outside of the drive receive most of the damage, leaving the delicate discs and heads intact. Many times, the information on the PCB is completely unique and often critical for accessing the data. If the crucial code from the remains of the PCB can not be read or the replacement code can not be written and a new board can not be rebuilt, data recovery is very difficult or even impossible.
5. chips
If you can find whole and undamaged chips on a motherboard, SSD or other flash media, the drive is likely also relatively undamaged and data can probably still be recovered.
what you should and should not do.
- Do not attempt to operate any devices that have been in a fire, even if it is just smoke-damaged, as this can cause unseen damage inside the hard drive.
- Do not shake, disassemble or attempt to clean any hard drive that has been damaged by a fire.
- Do not try to remove the hard drive. Instead, send the entire computer for recovery.
- Do not use data recovery software in case of a burnt hard drive.
- Do contact a data recovery specialist immediately, especially if your fire damaged hard drive stores valuable data on it.
*warning: A burnt hard disk is a physical damage condition, and a wrong decision can cause a permanent data loss.
With over two decades of experience in recovering personal and business data from burnt drives, using proprietary tools and knowledge, Kotar data recovery can assist you with data recovery from fire damaged devices.
post-pandemic summer travel and data loss.
It’s been over a year since we were told to cancel our travel plans due to the coronavirus pandemic. As more and more people get vaccinated and countries are reopening just in time for warm summer weather, travel is back. People are longing to travel again. Who doesn't want to go on a beach holiday again?
Summer is the perfect time to get outdoors, go swimming, hang out with friends, and enjoy the weather. For many, it’s also a time for graduations, weddings, vacations, and visiting family.
But in today's world, traveling is no longer what it used to be. It’s not just about packing a suitcase with clothes and books. Today, we can’t leave our homes without our portable devices: a laptop, tablet, camera, and a smartphone or two. Because digital devices have become a vital part of our lives, our privacy is at more risk than ever before when we travel. Our devices are loaded with personal information and pose significant privacy risks if not properly protected. Therefore, data safety has to be just as crucial as your personal safety, and protecting your data is just as important as protecting your valuables. Just as we keep cash out of sight and valuables locked away, we have to make sure to preserve our digital life when we’re away from home.
how to make a backup when traveling.
Unfortunately, being on the move means that the data on our digital devices is more vulnerable to loss. We’re often not careful backing up that data or even keeping track of the devices themselves. If your device is lost or stolen, you’ll be able to recover what was on it if you back it up during your trip. So don’t wait until you get home, but back up regularly, no matter where you are.
If you have access to Wi-Fi, you can back up your device to the cloud.
If you don’t have access to Wi-Fi, you can back up your devices to a USB thumb drive, an external drive or laptop and keep it safe. If you put it in with your luggage, make sure that it is not in the same bag where you carry your devices.
be careful with your devices when you travel.
Use covers and cases for your phone and cameras. It helps protect them from physical damage.
Keep your laptop or other devices with you wherever possible. If you need to leave it somewhere, for example in a hotel room, you should lock it in the room's safe.
Don’t leave any of your digital devices unprotected, for example in an airport security line, on a cafe or restaurant table, beside the pool, or in a handbag hanging from a chair.
Be aware of your surroundings, especially in a crowd.
Keep your devices away from all forms of liquid. Water is a common cause of damage to digital devices.
Ensure that your device needs a password or pin to be unlocked.
If your data is sensitive or critical, ensure that your device is encrypted. Encryption protects the confidentiality of your information by making it unreadable to anyone who does not have the right key (usually a password).
Don’t store sensitive data on unencrypted external devices (for example. memory sticks) that can be easily lost.
Install tracking or “find me” apps on your devices. Laptops, tablets, and smartphones are popular targets for theft because of their high resale value. There are several apps that can help you track and potentially recover your device in case it gets stolen or even lost. Some apps take photos of the perpetrator, geo-locate the device and even allow you to remotely log in and completely wipe your device to protect your information.
Always backup your data before traveling with your laptop or mobile device.
safety tips for using wi-fi on the go.
Public Wi-Fi networks are infamous for being places where criminal individuals snoop on other computers to steal passwords and account information. You can avoid that possibility by following some simple advice:
Password-protect and encrypt your devices. Don’t travel without setting a PIN, passcode, or pattern to lock down your mobile phone, laptop, and other devices.
Before you travel, it's recommended that you change the passwords on the accounts you plan to use. Change them again when you get home. Don’t use the same password on different accounts or reuse a password you’ve used previously. You can use password managers to handle your passwords.
Turn off sharing on your devices to prevent anyone obtaining access to your device.
Turn off automatic connection to open Wi-Fi networks.
Don’t use the web to access your bank, financial institutions, or other important sites if you’re not 100% confident in the security of your internet connection. If you do access a financial, shopping, or other high risk site, make sure your connection is protected with Secure Socket Layer (SSL), which is indicated with the HTTPS prefix in the URL. When you browse over HTTPS, people on the same Wi-Fi network as you can’t nose into the data that travels between you and the server of the website you’re connecting to. Sites that ask for payment or confidential information should use SSL. If they don’t, stay away.
You’re likely to use free Wi-Fi at a hotel, airport, cafe or mall when you travel. Unfortunately, these public networks are easily hacked, putting your passwords, your files, and personal information at risk. If you can, set up a virtual private network (VPN) to protect your connection. A VPN encrypts your browsing and internet activities and hides your IP so they stay private by routing your traffic through a secure network, even on public Wi-Fi. A VPN is a software program or app you install on your laptop or phone. You can turn it on when you go online, wherever you are.
Data loss and privacy risks won’t stop us from traveling, but we need to keep our privacy and security in mind at all times, whatever we’re doing and wherever we are.
In a world where we're more dependent on our devices than ever, data backup shouldn't be an afterthought. It should be one of the first things you consider when traveling. If you don't, you could lose your photos, your work files, or even your entire business.
Don't forget to keep your eye on your belongings and always take a proactive approach to backing up. But above all, enjoy your vacation - eat well and love every minute of your adventure.
And last but not least, if anything unpredictable happens and you do lose your precious data, Kotar Data Recovery has hands-on experience, extensive knowledge and state of the art tools to recover lost data from any device.
the digital world of photos.
In today's digital world, people continuously take photos and videos to save the moments they experience. It's like a life in review, sharing and preserving the best memories of every life's moment in the form of a digital diary. Therefore, losing a unique copy of photos and videos can be devastating and heartbreaking. Imagine losing your wedding pictures and videos, photos and videos of your children, or a vacation trip. Losing digital photos and videos can have a big personal impact.
For professional photographers, there is also an economic impact when photos and videos are lost or accidentally deleted. If, for example, a wedding photographer loses photos and videos from a couple’s big day, or an industrial photographer loses photos taken in industrial settings for catalogs and newsletters, or artistic images for galleries or shows, this can ruin their reputation and cause a decline in their business.
sd card.
Inside your smartphone, digital camera or other mobile devices, are usually SD cards. SD, or secure digital cards, are a small form of flash memory that has become popular with the rise of digital cameras and smartphones.
These tiny cards can hold a large amount of data. As you use your phone or camera, your SD card will fill up with priceless pictures and videos. But unfortunately, SD cards are very fragile storage devices, and vulnerable to physical damage. Therefore, they have to be treated with care and stored away from extreme heat or sunlight.
When you are taking photos and videos outside, keep your camera or phone safe from water and humidity and make sure to avoid drops and hits. Unfortunately, like any other storage media, SD cards can fail and all data can become inaccessible.
Your photos and videos will be safer if you invest in a decent quality memory card, rather than simply buying the cheapest one you can find. It is also recommended you buy multiple smaller capacity SD cards rather than a single large one. If anything goes wrong with one, fewer photos will be lost.
keep your sd card healthy.
SD cards are the sources of storing many videos and photos in digital cameras and mobile phones. They come with many advantages - for instance, they can be used in multiple devices, carry vast amounts of data, and make data transfers easy. However, you must be aware that any fault in the SD card could cause losing your precious data.
Take these basic precautions to avoid a memory card's malfunction and consequent data loss:
format the new SD card in your camera
It is advisable to format the memory card immediately after buying it. New SD cards are already formatted and ready to use, but reformatting will prepare the card according to the device’s hardware and avoid any harm.
eject the SD card safely
Make sure to eject your memory card safely and with the proper procedure. One of most common ways to damage the SD card is either turning off the camera before ejecting the card or improperly removing it once attached to the computer. These careless actions can be damaging to the SD card and to the data.
keep the SD card safe from environmental factors
Handle your card carefully and keep it in a case to prevent it from breaking, protect it from any moisture exposure or extreme temperatures or sunlight.
compatibility concerns
Always check on specifications of what your device will or won’t accept. For the SD card to work optimally and for a long time, make sure not to share your card with multiple devices and users. If sharing is essential, don't forget to store your data somewhere else first and reformat your card before using it.
lost photos can be recovered.
There are many ways you could lose your photos from an SD card. You could:
- accidentally format your SD card
- delete it by mistake
- the SD card gets corrupted
- there is a virus attack
- the SD card is physically damaged
In most cases, lost images on corrupt, deleted or damaged SD cards can be recovered.
If you, for example, accidentally press delete, the good news is that you don't lose your files permanently even after being deleted from the SD card. Your files remain as long as you don't take any action to read or overwrite the SD card. Data recovery critically depends on the actions you take just after realizing that you have lost valuable data. It is important to know that recovering photos from an SD card requires you to avoid overwriting them.
It is also important to know that data recovery from a physically damaged SD card is possible, but should only be attempted by a professional data recovery company.
Whether you’re an individual who’s just lost family photos and videos, or a professional photographer whose livelihood depends on getting the photos and videos you’ve lost back, the best way to increase your chance of recovering data precious to you is to stop using your SD card immediately once the data is lost.
where to store photos.
1. save to recordable media
SD memory cards are not suitable for long-term archival storage because the charge decays over long periods of time.
2. backup to your computer
Computers are a good backup option because they provide fast and easy access to your photos. However, a hard drive in your computer can fail at any time. To safely store your data, you should use at least two different storage medias, a desktop PC and an external USB hard drive that backs up the PC.
3. back-up to an external drive
External drives are convenient for storing photos because they can perform two important functions:
a) traveling drives allow photographers to keep digital images safe while on the move
b) back-up drives are part of the second stage, where digital images are backed up to a second device, or the cloud
4. cloud storage
Some of the more popular cloud storage options include Dropbox, Google Drive and Microsoft OneDrive.
Cloud photo services like Picturelife, Adobe Creative Cloud, and ThisLife make it easy to back up photos from iOS or Android devices as well as Macs or PCs, providing an additional layer of security, along with the tools necessary to organize and edit photos from anywhere, no matter what device or web browser you happen to be on at the time.
The general rule of a good backup is to have 3 different storage types, one of which should be off-site.
Make sure that you don't delete the photos and videos on your SD card until you are certain that they have been copied over to another storage device. After that, you need to back them up regularly either to a physical storage device like an external hard drive or RAID system, or in the cloud - or both if you want to be extra cautious. For professional photographers, it is worth keeping an additional backup off-site to protect their photos in the event of a fire or flood.
If you experienced SD card failure, lost your valuable photos and videos, and you don’t have a backup, contact a data recovery specialist right away.
Kotar Data Recovery experts have the technology and the expertise needed to access and successfully recover your data from any memory card and any data loss situation.
solid state drive.
SSD vs HDD.
Solid state drives (SSDs) and hard disk drives (HDDs) are the two main storage options. The type of storage your computer uses matters for the performance, power usage, and reliability of the computer. Therefore, choosing the right storage isn’t just about comparing capacity and cost.
Solid State Drives or SSDs got their "solid state" name because they have no moving parts.
An SSD consists of solid-state electronic memory chips to read and write data. Semiconductors alter the electric charges of these arrays, storing code in the process.
A HDD is essentially a metal platter with magnetic coating that stores your data. A read/write head on an arm accesses the data while the platters are spinning.
what makes SSDs so popular.
- What makes SSDs an increasingly popular choice is their speed. SSDs are faster, because their access time doesn't depend on a read/write interface head synchronizing with a data sector on a rotating disk.
- SSDs provide greater physical resilience to physical vibration, shock, and extreme temperature fluctuations. They are also immune to strong magnetic fields that can sanitize a hard drive.
- SSDs in general are more reliable than HDDs.
- SSDs are smaller and weigh less than HDDs, which is especially important with laptops.
- SSDs are more power efficient than HDDs. SSDs commonly use less power and result in longer battery life because data access is much faster and the device is more often idle.
- SSDs make no noise at all because they're non-mechanical.
- SSDs are more expensive than HDDs per amount of storage (in GB or TB), but the gap is rapidly closing as SSD prices quickly begin to drop.
do SSDs fail.
SSDs can fail, but in a different way than traditional HDDs. While HDDs often fail because of mechanical issues, SSDs may fail due to the methods used to write information.
SSDs use flash memory cells to store data. In this way, SSDs function almost like large flash drives, programming data onto these cells by changing their electric charges. However, once you fill the available memory on an SSD, the SSD can only add new information by erasing older data. This process is called a program/erase cycle, or P/E cycle.
Importantly, each SSD has a limited number of P/E cycles. Each P/E cycle gradually degrades the memory of an SSD’s cells until they eventually become worn down. At this point, you will no longer be able to rely on the SSD to store information. The gradual wearing out of SSD flash cells means the drive will no longer be usable.
While SSDs may fail with less frequency than HDDs, they do have a higher error rate that can affect the end-user experience. So-called uncorrectable errors are relatively common in SSDs. They can affect data retention and lead to effective failure.
warning signals for SSD failure.
Unfortunately, SSD failures are hard to detect. Unlike HDDs, SSDs do not emit audible signals like whirring, clicking, or humming when they’re approaching a complete shutdown. SSDs can operate in silence until they simply stop functioning.
Typical SSD failure symptoms include slow transfer rates, repeated file access issues, file corruption, and a large number of bad sectors.
Here are some of the most common indicators that your SSD is failing:
- Bad blocks for saving files, low speed for copy or transfer files, failed files transfer.
- Your computer shows the following notification: 'file system requires repair'.
- Your computer crashes while booting up but detects the drive after a few reboots.
- Your SSD operates in 'read-only' mode.
- This message appears: 'operating system not found'.
- External USB drivers can not be detected.
common causes of SSD data loss.
Data loss can be caused not only by SSD failure but many other factors:
- Human error
- Viruses and malware
- SSD damage
- Power outages
- Computer / laptop theft
- Liquid damage
- High temperatures
- Disasters (fires, storms, floods)
- Software corruption
- SSD formatting
- Hackers
how to prevent unexpected SSD data loss.
While SSDs are considered reliable, there is still the possibility of drive failure and data loss. Here is what you should do in order to prevent data loss:
- Backup important data to another drive or external storage device.
Backup data regularly and routinely, even if your SSD appears to be in good health. Unexpected corruption, power surges, viruses, or physical harm could hit your drive and cause permanent data loss. You truly never know what can happen, which is why valuable data should always be duplicated somewhere secure. - Download and install anti-virus software to scan and remove all viruses from the SSD drive.
- Download a program designed to monitor SSD health by tracking operating temperature and performance metrics.
- Make sure that you always leave a portion of your SSD empty to ensure that the leveling algorithms work well. These algorithms are responsible for redistributing data to minimize the wear and tear on the drive and keep it functioning optimally.
- Stop using your SSD immediately when you find data loss trouble has occurred to your drive. SSDs' issues are often progressive, which means that they become worse as the drive continues to operate.
- Call a professional data recovery company to help you protect and retrieve your data.
- When investing in a new SSD, buy strategically. Many SSDs come equipped with S.M.A.R.T. (Self-Monitoring, Analysis, and Reporting Technology) that warns users of potential failure and prompts them to take preventative measures.
SSD Data Recovery
Due to the completely different mechanics and working methods, SSD data recovery greatly differs from HDD data recovery, and requires a special set of knowledge and tools.
The latest SSDs come with complex and highly proprietary features. SSD controllers contain ever-evolving technologies like compression, de-duplication and high-level encryption protocols. They protect the security of stored data and provide greater data protection than HDDs. These complex features can present a challenge for data recovery and engineers need to use a specialized process to recover data from an SSD.
If your SSD has failed you and you have lost your critical data, Kotar Data Recovery experts can help. We have a long history of expertise with SSD data recovery and can recover data from any make, model, or brand of SSD using proprietary tools and techniques.
external drives.
what is an external drive.
An external drive is a hard drive (HDD) or a solid state drive (SSD) that is typically attached to a computer via a USB connection. An external drive is a portable storage device that provides a large amount of storage whenever you need it and allows you to carry a large number of files with you wherever you go. It usually comes with large storage capacities and can be used to store files from multiple devices.
hdd vs. ssd external drive.
HDDs are mechanical and contain moving parts, such as mechanical platters and moving read-write heads to access data. This makes them more vulnerable to physical damage due to accidental drops and other shocks, vibration, extreme temperatures, and magnetic fields. Because of these, external hard drives have a higher probability of a physical fault, such as a head crash or motor failure. HDDs are more affordable, offer more storage space than most SSD models, but they are larger and use more energy.
SSDs use flash memory chips and are entirely solid - have no moving parts and are therefore more durable. They are immune to magnetic fields and can withstand more shocks and vibration than hard drives. They also weigh less and aren’t as energy-intensive as HDDs. SSDs tend to deliver faster performance because of the way they process, store, and access data. However, once SSDs are full, they can only write new information by erasing older information, same as HDDs. The difference is that flash type memory cells can only be programmed and erased a limited number of times. Over time, this creates wear and tear on flash cells and ultimately renders them unusable. While SSDs cost a lot more per gigabyte, their prices are continuously dropping.
uses of external drives.
storage.
Every computer, desktop or laptop, is equipped with an internal hard drive. Whenever you save a file, photo, or software to your computer, it’s stored on your hard drive. External drives can be used as supplemental storage to the storage already on your computer. For example, if your computer is often giving you low disk space warnings, it's working hard to keep things running on the little bits of free space it has left. This can lead to slowdown when playing games, streaming movies, running programs, or even just browsing the web. If you have a large amount of high-definition photos and videos that are slowing your computer down, you can copy some of your files on your external drive to free up storage on your primary hard drive. External drives are commonly used to store files that we don’t access very frequently, like old photos or videos, records and archival data or completed projects.
backup.
We store so much valuable information on our computer drives - from photo and video collections, to work files and financial documents. One of the most important things you can do to protect your computer data is to back up your drive. A backup is just a second copy of your drive that you’ll have available in case something happens to your computer. You should be making backups as frequently as possible. Be sure to store these drives in different locations so they won’t be exposed to the same risk of environmental damage or theft.
If you are using an external drive as a backup for your data, make sure that there will always be a second copy.
data sharing.
External drives are great for moving files between computers, regardless of their operating system. Whether you’re trying to transfer data from an old computer to a new computer, trying to exchange data with a business partner, or if you have an album on your PC that you want to share with your friend who has a Mac, all you need to do is put the data on an external drive, and then connect the external drive to whichever computer you want to transfer the data.
editing.
An external hard drive is indispensable for digital editing when you work with libraries of large image files, digital illustration, or in audio or video editing.
gaming.
Modern PC games are massive in scope and graphical detail and take up a lot more space on your drive. Your computer won’t perform as quickly if you’re running low on free space. If your drive is getting filled with games, get an external drive to store them on.
reasons for data loss from external drives.
Most common reasons for data loss from external drives are connected to our everyday lives and the way we save, store, and handle our data:
1. Deleting files accidentally
2. Viruses and malware
3. Mechanical damages
4. Power failures
5. Theft
6. Spilling and other water damages
7. Fire accidents
how to protect external drive data and avoid data loss.
- Handle your external drive with care to avoid drops, spills, and other damage.
- Keep it out of direct sunlight and do not expose it to extreme temperatures or moisture.
- Keep your external drive safe. Don't leave it unattended on top of your desk where it could be an easy target, especially when working in public places.
- Make regular checkups on your drive and address any error message immediately. There are several freeware programs online to perform regular drive checkups.
- Keep your drive under storage capacity. Filling your drive close to capacity forces the drive to work harder for access which increases wear and tear.
- Always select the “Remove Device” option instead of just pulling your drive’s USB out of your laptop or computer. This will decrease the likelihood that your data transfer will be interrupted and corrupted and prevent your drive from suffering the power surge commonly associated with improper unplugging.
- Have more than one copy of data that is very valuable or that can not be recreated. You can make a full copy to another device of similar or greater capacity or back up your external drive to the cloud.
- Label external drives to minimize the potential of accidentally formatting the wrong device.
what do to when you lose external drive files.
Stop using your external drive immediately because new data is highly likely to overwrite lost data, which will make the lost files unrecoverable. If you can't get your operating system to recognize the drive, your best option to restore the data is to engage a professional data recovery service.
Kotar Data Recovery, with 22 years of research and expertise, can successfully recover your valuable data from failed external drives.
importance of data backup.
why you should back up.
Imagine what you would do if you lost all your data. There are several scenarios where having a backup of your data would
be extremely useful:
- your phone or your laptop gets stolen, resulting in you losing all your pictures, videos, and work
- a hard drive crashes
- a ransomware holds your data hostage until you pay to remove the restraints
- you accidentally delete something important
your data is more valuable than your device.
You can get a new computer or phone, but you can't replace your important business data, your term paper, or the photos & videos of your little girl or boy. Therefore, you have to back it up.
The purpose of a backup is to have a recovery plan should the primary data become inaccessible. Technically, a backup just refers to any piece of data that exists in two places. When you back up your data, you make a second copy of anything and everything that you don't want to lose. In case something happens to the originals, you will be able to restore the backups to your device (computer or phone). However, if the only copy you have of your important files is all in one place, it only takes one accident, one small disaster for you to lose them all.
the golden rule of backup.
The 3-2-1 rule of backup:
- keep at least 3 copies of your data (an original copy and two backups)
- maintain 2 local copies on different types of backup media
- have at least 1 backup solution hosted off-site (i.e. in the cloud)
the question of data loss is not "if" but "when".
As more and more of our lives migrate online, ways to lose our data are rapidly increasing. While there used to be time when we could limit our concerns to hard disk failure or device theft, today’s users know it could also be corrupted by malware or ransomware. Cybercriminals are well aware that personal and business data hold tremendous value.
At the same time, backup and recovery solutions today are affordable, simple to manage, and a little effort could end up saving your precious photos or essential business data.
backup vs. insurance.
Most people understand why they need to buy insurance for their cars and homes. Insurance provides financial recovery in the event of an accident or loss - and we hope that we will never need to file a claim to recover from losses. Backing up your data is similar to car or home insurance in that both are needed to recover from losses. However, there are some major differences.
Insurance is usually intended to protect against unexpected losses. You don't expect your house to burn down, or to have a car accident. You may not expect your hard disk to fail either, but this is where the big difference comes in. Eventually, every hard disk will fail, or your phone will get lost or broken, you will accidentally delete something important, or a virus/ransomware will hold your data hostage until you pay - and you will certainly need your backup.
Can you imagine how much your car insurance premium would be if you were certain to have an accident? In many cases, the insurance companies charge you based on your driving record. So when you do have an accident, your premiums are probably going to go up.
However, your backup doesn't get more expensive based on how many losses you have experienced in the past. And the cost doesn't go up as soon as you lose your data. Data backup is actually a great deal when you consider the value that it is protecting.
March 31st is World Backup Day.
March 31st is world backup day and we think it is appropriate to remind us all of the increasing role of data in our lives and, consequently, of the importance of regular backups.
Whether you’re an individual or a business, take a moment to consider all you have to lose and backup your critical data today. If you already have a backup solution in place, make sure it is working correctly and backup is performed frequently, e.g. daily or whenever the data is modified.
If you lost your data and backup failed you, our data recovery experts can help to recover your valuable data from any device with complete privacy and security.
encryption.
what is encryption.
Encryption is the method by which information is converted into a secret code that hides the information's true meaning. It helps provide data security for sensitive information.
how encryption protects your data.
When you encrypt your files, they can only be read by the person who has the secret code or decryption key. This means that if someone steals your files, they won’t be able to do anything with them.
Encryption helps protect the confidentiality of digital data either stored on computer systems or transmitted through the internet. We use devices every day to send, receive, and store a vast amount of personal data, logs or banking information.
Therefore, encryption is a very important tool for keeping your digital data safe. When the intended recipient accesses the message, the information is translated back to its original form. This is called decryption. To unlock the message, both the sender and the recipient have to use a decryption key that brings data back to a readable format.
why encryption is so important.
Internet privacy concerns
Encryption helps protect your online privacy by turning personal information into encrypted messages intended only for those they are meant for.
Hacking danger
Cybercriminals are often out to steal personal information for financial gain.
Regulations
Encryption helps businesses stay compliant with regulatory requirements and standards. It also helps protect the valuable data of their customers.
two types of encryption.
Software encryption
Software encryption uses software tools to encrypt your data and typically relies on a password. If you enter the correct password, your files will be decrypted - otherwise, they remain locked. Software encryption is typically quite cheap to implement and is therefore very popular with developers. However, software encryption is only as secure as the rest of your computer or smartphone. If a hacker can crack your password, the encryption is immediately undone.
Also, software encryption tools can cause the whole machine to slow down as data is encrypted/decrypted. Along with that, opening and closing encrypted files is much slower than usual.
Hardware encryption
A separate processor is dedicated to the task of authentication and encryption. Hardware encryption is increasingly common on mobile devices, like the TouchID fingerprint scanner on Apple iPhones. Hardware encryption is considered to be safer than software encryption because the encryption process is kept separate from the rest of the machine. This makes it much harder to intercept or break. Because of the use of a separate processor, the encryption/decryption process is
much faster.
On the negative side, the hardware-based encrypted storage is usually much more expensive than a software tool. Plus, if the hardware decryption processor fails, it becomes extremely hard to access your information.
the data recovery challenge.
Encrypted data is extremely hard to recover. Even if the raw sectors are recovered from a failed drive, the data is still encrypted – meaning it is still unreadable. Some software encryption systems have built-in recovery mechanisms, but you need to have your recovery options set up in advance.
Hardware encrypted devices don’t typically have these additional recovery options. Many are designed to prevent decryption in the event of a component failure, stopping hackers from disassembling them.
For computer systems, the fastest and most effective way to deal with data loss on an encrypted device is when you copy data to another encrypted device and have a complete backup stored somewhere else. For smartphones, backing up to the Cloud provides a quick and economical copy that you can restore from. Nowadays, most Cloud services encrypt their users’ data too.
If you lose data on your encrypted device, our expert engineers can advise, help, and most likely successfully recover your data.
Kotar Data Recovery has the tools and knowledge to deal with encrypted projects.
covid fatigue and data loss.
After months of social distancing, sheltering in place, working and
schooling from home, mask-wearing, hand-washing and being careful, we
are becoming fatigued. Unfortunately, fatigued people are prone to
getting careless.
When people are under stress for an extended period of time, they grow
tired of being required to constantly employ protective measures. This
is especially true when the threat is not perceived as imminent or
direct, or when it is invisible.
Covid fatigue can be described as denial and careless behavior as a
result of feeling overwhelmed and exhausted by a constant stream of
pandemic-related information.
It is related to a caution fatigue, a really low interest in taking
safety precautions, which can lead to dangerous choices for the health
and safety of people in the real world and online.
Covid fatigue is also closely connected with security fatigue which
prevents users from taking definitive steps to protect themselves
while connected to the internet. Because COVID-19 has forced us to
spend a lot more time online, it has driven us into the open arms of
the internet like never before and opened the gates for cybercriminal
activity.
Covid fatigue, along with anxiety and burnout, calls for human error,
especially so when using computers, laptops, phones, and other
devices. As we know, human error is not only a significant cause for
cyber-attacks, ransomware, and data breaches, but also the leading
cause of data loss. Human error can result in the accidental deletion
or overwriting of data. It can also play a role in many other main
causes of data loss, including hard drive damage, liquid spills,
software corruption, and hard drive formatting.
Data loss and cyber attacks are a constant threat in the digital age.
That is why we need to exercise even more care and take precautions,
not letting Covid fatigue transform into frequent human errors,
compromised cyber security, and data loss in these unprecedented
times.
Here are the five rules we should try to follow:
1. Backup your data regularly.
2. Encrypt sensitive data.
3. Use a password manager.
4. Use an anti-virus software on all your devices and keep it updated.
5. Use common sense.
If you lost your data and can’t find a backup or your device was
infected by ransomware, stay calm and call a data recovery specialist
who will be able to give you advice on what to do.
Kotar Data Recovery has the tools and knowledge combined with decades
of experiences to recover your precious data.
data protection.
As we're entering the 2020 holiday season and Covid-19 cases are continuing to rise, the most affected regions have already started implementing new stay-at -home orders. As a result of all these, we’re witnessing the 2020 work from home revolution. A number of top executives have already announced that they will allow their employees to work from home not only during the duration of this pandemic, but also beyond.
If you're working from home or are living in a region with stay at home orders to take care of your physical health, now is the right time to also take care of your digital health.
To present an important topic in a more holiday-themed reading, we wrapped our tips into the "12 Days of Data Protection" in the spirit of the merry season.
On the first day, review and evaluate your backup practice.
Do you back up your data?
How often do you back up your critical data?
On the second day, check your backup.
Does it work properly?
On the third day, check your power protection devices.
Are they functioning well?
Do you have working universal power supply in place?
On the fourth day, check your surge protector.
Do you have it in place?
On the fifth day, check and evaluate any offsite data centers.
Do they comply with the first four steps?
On the sixth day, review the offsite media storage.
Do you know what content is on there?
On the seventh day, catalog tape media, if any, to make it easier for you to manage.
Do you have any tape media without labels?
On the eighth day, check the media that is defective or you don't use anymore.
Do you want to sell it or just send it to silicon heaven?
Did you securely erase your data from the media?
On the ninth day, evaluate your erasing process.
Did you effectively wipe or physically destroy your media to make sure your data is 100% gone?
On the tenth day, check your data encryption.
Did you log your encryption software somewhere safe?
Do you know all of your passwords?
On the eleventh day, check any cloud storage.
Are you familiar with your cloud provider’s protocol for data that is lost?
On the twelfth day, check for a plan for data recovery should (God forbid) data loss occur to you.
Do you have a data recovery plan?
Do you know how to proceed and who to turn to?
If you experience data loss, Kotar Data Recovery, a Silicon Valley data recovery specialist since 1999, is committed to do everything in their power to recover your valuable data.
We wish you a happy, healthy, and safe 2020 holiday season.
data confidentiality.
At Kotar Data Recovery, we are aware that in today’s world, privacy is
more important than ever.
Data security and confidentiality is and always has been, the biggest
priority within our company. Therefore, there is nothing more
important to us than keeping your data completely confidential and
secure.
We regularly work with customers who range from individuals and
businesses, from small to those listed on the Fortune 500, to
government agencies, hospitals, forensic companies, etc., all of whom
have highly sensitive data. We apply the same data safety policy and
implement the same security measures for every single data recovery
case. Sometimes, additional measures have to be taken to guarantee
that the customers' data is kept completely private and secure. In
special cases, we need to work with a company’s legal department to
address any specific needs they may have and possibly sign their
non-disclosure agreements.
We are willing to work within any reasonable requirements that may
need to be met so that our customers can rest assured that their data
will remain 100% secured and confidential throughout the recovery
process.
To keep your data safe, none of our data recovery servers are
networked in any way, which guarantees that there can not be a data
security breach within our network. This means none of your
information will ever be shared peer-to-peer or by network intrusion.
We have a strict non-disclosure agreement and all of our employees
comply with this agreement.
We also make sure that only the engineer working on your data recovery
case has access to your data during the data recovery process. You
don’t have to worry about them looking through your information
because we can not actually see your data. During most of the recovery
process, your drive is being imaged. During this imaging process, we
can view the layout of your data on your media. But since we work on
the low data level, this means that we actually can not see the data.
We can only see the sectors and the raw data associated with each
sector. We do not use a graphical user interface which would allow us
to view the information on a hard drive.
Once the imaging process is complete, we will know which areas of the
drive couldn’t be read. We will then make a final pass over those
unreadable areas to try and read as much data as possible. Then we
will tree up the directory to make sure that the file structure is
intact. After that is finished, we then mount the cloned disk to our
recovery server and begin transferring the image to the destination
drive that will be given to you. It's not until the end when we are
copying the data over to the destination drive, that only Robert Kotar
(the CEO and owner) has access to the data exclusively to verify that
the data has been successfully recovered. He may open a few files,
randomly spread out throughout the drive, just to make sure that the
files are indeed intact.
We hold on to the cloned copy until the customer confirms the
recovered data is ok. At that point, we securely and completely delete
all the data for safety and security purposes.
At Kotar Data Recovery, we have been successfully recovering data for
thousands of clients since 1999 with a strong commitment to security
and confidentiality. We greatly respect our clients' privacy and we
guarantee that your data will remain absolutely secure and
confidential throughout our data recovery process.
when do you need a data recovery specialist.
Data loss is a common issue that all of us have experienced at some point. Unfortunately, sometimes we lose an important piece of data. In such cases, data loss can be very frustrating, costly, and even disastrous.
A company's most valuable assets are often its digital files and records. They contain the sum of a company's work, including employee and tax records, proprietary technology, as well as software licenses, customer records, and any investments it has. Data loss is not just inconvenient, it's potentially a death sentence for a small business. Imagine not being able to check in on an order's status, getting access to your factory's production software, contacting a customer, or checking whether an invoice has been paid.
This is certainly a frightening scenario, however, in most cases of data loss, the missing data remains on your storage media and can probably be restored even if you can not see it.
In the event that you lose your precious data and you don't have a useful backup, you need to consult a data recovery expert. They are your best shot at getting your lost data recovered. Do not try to recover the data yourself, because the first data recovery attempt is critical, as it provides the best chance of successfully recovering your data. An unsuccessful first attempt can further damage your data. If your hard drive crashed and you hear any clicking or grinding noise, your hard drive could have some physical damage. Do not attempt to retrieve data by using utility software, since continued operation of your hard drive is likely to result in more harm.
how to find a reliable data recovery company.
Hundreds of small services promise data recovery but they are nothing more than intake centers for larger recovery firms. A good indication of their abilities is if they have a cleanroom onsite for repairs, stock the parts needed to fix a variety of drives quickly, if they have strict security protocols in place, and if they can recover data from all sorts of digital storage devices – computer hard drives, SSDs, laptops, RAID arrays, NAS, file server drives, phones, tablets, cameras, flash drives, SD cards, etc.
It is important to check if a data recovery company offers a "free estimation" because you don't want to spend money only to find out if the data is recoverable or not. Data recovery experts will examine your storage media and determine if the data can be recovered, how long it will take, and how much the data recovery would cost. If the data is not recoverable, they will send you your storage media back, and will not charge you any fees.
Along with that, check if a data recovery company has a "no data, no charge" policy, since you don't want to end up paying for unsuccessful data recovery attempts that will not be able to recover any of your data.
It is also important to check if they have a Class 100 cleanroom as a dust free environment is essential for fixing hardware issues such as burned-out motors, damaged platters, or worn out read-write heads.
Having a recommendation can also help in your data recovery decision. It is advised to check Google and Yelp reviews of any data recovery company that you are considering.
If your storage media broke down, if you’ve accidentally deleted your files, or if your business’ server has crashed, Kotar Data Recovery experts can fix multiple data failures and get your data back from any type of storage media.
Kotar Data Recovery offers free consultation, free estimation, free pick-up & delivery, a no data-no charge guarantee, a free complete data wipe and free secure disposal of the original drive when the work is done, a class 100 cleanroom, and 24/7 live support.
how to disinfect your electronic devices.
The COVID-19 pandemic has altered life as we know it and it is going to stay with us well into 2021. Among other measures to protect yourself and others from the virus, the CDC also recommends frequently cleaning and disinfecting frequently touched surfaces. This includes phones, laptops / computers, keyboards, and other electronic devices that we use every day.
Because we are always carrying our cell phones with us, their surfaces tend to carry a lot of germs. In fact, our own hand is the biggest culprit when it comes to putting filth on our phone. According to a survey by Deloitte, Americans check their phones about 50 times per day. Every time you touch your phone, the phone picks up germs from your hands. A study by the University of Arizona found that cellphones carry 10 times more germs than a toilet seat, because people clean toilet seats but they seldom clean their phones. The same goes for their laptops or desktops.
Especially in the time of the coronavirus pandemic, if you touch your phone after touching a public door handle or grocery cart, you should immediately think of cleaning it.
So, what is the correct way to disinfect devices without damaging them?
1. Power down your device and unplug all external power sources, devices, and cables.
2. Ideally, check with the manufacturer of your device for the best cleaning methods.
Since devices come from various manufacturers, practices may vary, although there are some common guidelines that you can follow no matter what brand your device is.
Apple f.e. used to tell people not to use disinfecting wipes on its products but the company now says it is okay to use a disinfecting wipe (such as Clorox or other wipes with 70 percent isopropyl alcohol) on the hard, nonporous surfaces like the display, the keyboards and other exterior surfaces as long as you don’t use bleach and avoid getting moisture in an opening.
3. Use anti-bacterial wipes to gently wipe the hard, nonporous surfaces of your device, such as the display, keyboard, or other exterior surfaces.
You can also use a soft cloth with a product that contains 70 percent isopropyl alcohol, but make sure the cloth is lint-free. Otherwise, it will leave fluff behind. Avoid any material that could be abrasive, like rough towels or paper towels, as these may damage the sensitive screen.
Don't use aerosol sprays and window cleaners, as well as cleaning products with abrasives, hydrogen peroxide, chlorine, acetone, ammonia, or bleach, as these may discolor or otherwise harm your devices.
4. Never spray any cleaner or disinfectant directly onto the device. Instead, spray it on the cloth and then use the cloth on the device.
Keep liquids away from the device. Make sure that no liquid gets inside your device through any openings because it can ruin your device and most insurance doesn't cover liquid damage.
Never dunk your phone, laptop or keyboard in a cleaning agent.
5. Other parts of the phone such as the power and home button, not just the screen and keyboard must be cleaned too.
6. Don’t forget your phone case. Clean it and let it dry before slipping your phone back inside.
7. If you love tech, you can try a UV phone sanitizer that uses UV-C light to break down germs.
8. Remember that your TV remote, game controllers, and other electronics should also be cleaned, not just computers and phones.
Please keep in mind that cleaning your devices is not of much use if you don’t clean your hands regularly as well. Self-discipline is key.
If anything unpredictable happens to your device and you lose your data, Kotar Data Recovery can always reverse time and bring your data back.
Stay safe and healthy.
road trips and data loss.
The world of 2020 is quite unexpected. In order to maintain social distancing while still getting out of the house, many people are planning to take a road trip this summer. Since portable devices such as laptops, iPads and smartphones have become an integral part of our life, people will naturally take them on the road. They are also extremely useful and we can create a large amount of data with them every day by taking photos and videos.
While on the road trip, we must not forget that all common causes of data loss, such as human error, hardware failure, computer viruses, software corruption, moisture, mechanical damage, theft and loss travel with us. In addition to these, we often forget that heat in a hot car can damage our electronics as well and potentially cause data loss.
Here are some tips for keeping your electronic devices safe and minimize data loss in the summer heat:
1. Don't leave your devices in a hot car because prolonged exposure to high temperatures can negatively affect their mechanisms. If you really must store your devices in a vehicle, keep them in padded cases and place them in the trunk or underneath a seat out of direct sunlight. Hiding your phone, laptop, or camera in the trunk of your car may trick thieves, but it won't prevent heat damage.
2. Keep devices in the shade when not using them. If you are outdoors and having fun in the sun, find a shaded place to store your devices.
3. If you need to use your devices outdoors for a longer time, stay in the shade to protect your devices from the damaging sun.
4. Store your devices in a thermal cover which will keep them much cooler than if left out in the open.
5. Don’t leave the screen facing the sun. Long exposure to the burning summer sun can bleach the screen.
6. It is important to stay careful when you come back inside as well. Keep electronics out of direct sunlight and make sure that your room doesn’t get too hot for your devices.
7. Back up your data regularly.
If something goes wrong and you lose your data: don't panic and act rationally. Kotar Data Recovery has 20+ years of data recovery experience, including from devices that have been damaged by extreme conditions such as heat.
But most importantly, use common sense and stay safe and healthy.
summer weather and data loss.
We all like warm and sunny summer days. But unfortunately, summertime is not as fun for our electronic devices such as laptops, desktops, servers, smartphones, etc.
Summer heat can quickly turn into severe weather conditions that can generate fires, storms, floods, extreme heat, and strong winds that lead to electrical surges, power outages, overheating, and high humidity that can generate electrical failure and cause data loss.
Fires
Droughts in the summer present an increased risk of fires, especially in California. Fire can destroy a computer's hard drive and cause data loss.
Floods
With summer thunderstorms falling rapidly, floods are common in the summer months. Flood water in a house can damage any computer placed on the floor or with wiring close to the ground.
Storms
During storms, electrical surges and power shortages are common and can cause data loss.
There are different scenarios of how a hard drive can be damaged by electrical surges, power outages and other natural disasters:
1. Read/write heads repark incorrectly
Because computers and operating systems are complex, they need to shut down properly. An outage causes computers to shut down suddenly and improperly. This can cause any open files you have been working on could to be lost or become corrupted. If power outages occur frequently, they can damage your hard drive and reduce its lifespan.
How does this happen?
When a hard drive runs, its platters spin and generate an air blow that keeps the read/write heads floating above the surface. During a normal shutdown, the heads repark back into place before touching the platter’s surface. However, when power is suddenly cut to a drive, the drive’s read/write heads repark incorrectly. The platters slow down to a stop, unexpectedly removing the air that keeps the heads off the surface of the platter, causing harmful contact between the heads and the platters. This is what we call a "head crash". It can damage the read/write heads or scratch the surface of the platter. As a result, the hard drive can fail and data can be lost.
2. Damaged control board
Electrical surges are usually caused by lightning strikes during storms. Lightning sends high levels of voltage through power lines. If a computer is plugged in during a power surge, it can be damaged. The damaged components often look charred or burnt. These can prevent a drive from powering up which leads to data loss.
3. Damaged read/write heads
Electrical surges can also damage read/write heads of a hard drive. The read/write heads of a hard drive are very sensitive and handle very little power during normal operation. A hard drive control board prevents heads from too much power reaching them. However, during electrical surges the protective components on the control board can be damaged. This causes high levels of voltage and current to reach and damage the delicate read/write heads. If this happens, data is not accessible.
Power surges usually damage the control board after receiving too much power, consequently causing the read/write heads to short out as well.
How can we prevent hard drive damage and data loss?
1. Surge Protector
Use a surge protector to protect your computer from unexpected power surges. Instead of plugging devices directly into an outlet, plug them into a surge protector, which plugs into a regular outlet. If an electrical surge happens, the surge protector offers protection from the spike in voltage. Surge protector channels the extra voltage through its grounding wire instead of the devices plugged into it and protects electronics from damage. However, surge protectors can only help prevent damage due to minor electrical surges, usually caused by heat waves when power usage increases due to high demand for f.e. air conditioning. Increased levels of usage can cause voltage to temporarily drop, then rise again which often causes power surges.
2. Unplug Your Devices
Electrical surges caused by lightning during a storm are strong and a standard surge protector often can't help. Therefore, the old good way of powering down and unplugging your electronics is the safest way to protect them during a thunderstorm.
3. Backup Your Data
The best way to protect from any data loss situation is by having a good backup strategy. We recommend a secure online backup solution which stores your files offsite so there is no risk of data loss due to electrical surges, fires, or floods. If you do backup on physical storage devices like flash drives or external hard drives, the same disaster can destroy both the data on your computer as well as your backup data.
In case there is no backup, Kotar Data Recovery can always help and recover your lost data.
backup.
How to backup your data
In today’s fast-paced world, it's essential to have a comprehensive backup strategy in place. With so many ways to lose data: media damage, human error/accidental deletion, cyberattacks, theft, rogue employees, natural disasters, etc; it is critical to understand how to backup your data properly.
Typically, music, photos, movies, critical data files, financial records, projects (the data you’ve spent so long creating and accumulating) are all stored in one place: your computer. But having all of your data in only one place is dangerous.
Losing data can be troublesome and heartbreaking for individuals, but for organizations, the repercussions can be irreversible. Many companies that experience severe data loss go out of business.
What is a good backup strategy
Ideally, we recommend a 3-2-1 backup strategy. This means:
- Keep 3 copies of your data
(one is your original copy, the other two are backups)
- Keep 2 copies on 2 different storage types
(NAS, external hard drives, flash memory, magnetic tapes, cloud, etc.)
- Keep 1 copy off-site
(outside of your location or company premises)
A good way to start is by having the original copy of your data, along with an external hard drive at your location, and an off-site cloud backup.
Why does this work
3: Storing the same data three times statistically minimizes the chances of data loss.
2: Using two different data storage technologies further reduces the probability of data loss occurring.
1: Keeping a backup in at least one other location is always recommended because if there is a fire, flood or other disaster, theft or cyber-attack at the principal site, not all backups will be lost.
What is a good backup system
There are many ways to backup your data. Even a manual copy, like saving a copy to an external drive, is some kind of backup. However, it is not very reliable, because you have to do it manually, repeatedly, and you have to manage things like deleting and renaming files. A good backup system automatically performs incremental backups so you don’t need to think about it or remember to do anything about it once the system is set up.
Conclusion
If you don't have your backup strategy in place, you should act immediately. Because all hard drives will eventually fail, it’s just a question of when and whether or not you’ll be prepared.
If you lost your data, Kotar Data Recovery can recover your data from any kind of media including HDD, SSD, RAID, server, USB drives, SD cards, mobile phones, etc.
causes of data loss.
Data is a vital asset to any company. Imagine the value of client databases, technical inventions, industrial information essential for manufacturing, or financial transactions' history of companies. If that data is lost, a huge part of a company's value is gone. On top of that you could also potentially be hit with a large fine.
Data is increasingly valuable, but also vulnerable.
The primary causes of data loss are:
1. Human Errors
Human error is one of the most common causes of data loss. There are two kinds of human errors causing data loss:
- Deleting or formatting files accidentally without having any backups available.
We often accidentally delete wrong files or overwrite the parts we did not intend to.
- Causing physical damages by dropping a storage device by accident, spilling liquids on computers (especially laptops) or dropping a device (especially smartphones) into water.
2. Mechanical or electrical (electronic) damages to the hard drive or SSD
Hardware malfunctions are the most common cause of data loss. Hard drives are the most fragile parts of computers; they break down more often than any other device connected to computing. There are so many moving parts inside of hard drives that it is no wonder they break down so easily. Along with hard drives just dying their natural death, there may be numerous manufacturing defects due to the need for storing more and more data on the disks of limited size. SSDs with the NAND Flash-based chips have a limited lifespan by default since data can only be written on a storage cell inside the chips between approximately 3,000 and 100,000 times during its lifetime.
Memory devices are also often damaged when computers are accidentally dropped.
3. Viruses and Malware
Being connected to the internet has many advantages, however, it also exposes computers to many risks. The majority of viruses affect operational software, misuse internet connection and damage stored data. There are many different types of viruses and frequently data loss is just a side effect of a greater damage done to your operational system. The most dangerous are the attacks targeted to steal and damage business data. Where there is a monetary value, there is also a strong interest to acquire this information.
4. Power failure
There are two effects of power failures:
- If you lose power while working (writing an article, working with databases or creating graphics), and you haven't saved your work yet, you lose your data.
- Power failures can affect operation systems or hardware of computers. Shutting computers down suddenly may cause problems with rebooting the operation system later and your data might not be accessible anymore. Sudden changes in voltage may damage different computer parts. Most problems can be solved by changing the power supply unit, but other hardware parts of computers (like hard drives or SSDs which are very sensitive to changes in voltage and strong magnetic fields) can be damaged as well.
5. Natural disasters
Natural disasters such as fires, floods, tornados, and earthquakes are the most uncontrollable, but fortunately also very rare causes of data loss.
6. Public health crisis
This is a brand new cause of data loss.
The world has changed during the coronavirus pandemic. People and businesses are adjusting to the new reality of social distancing, working from home and using new technologies.
When people are working from home, they can experience many disruptions, from loneliness to interruptions from family, pets, even delivery people. There can also be technology hiccups from new hardware or video call/meeting apps to internet outage and unstable and slow internet connection. People can experience computer, laptop, tablet, or mobile phone breaks, viruses, hacker attacks and cyber security threats.
During a pandemic, technicians and maintainers may not be able to get to your site as normal and repair devices that need maintenance. Even the supply lines to receive parts or materials may be adversely impacted.
Reopening the coronavirus economy gradually with safety precautions suggests using technology to limit human contact and reduce interactions. This will bring new challenges as living with COVID-19 will become our new normal as a society.
All these disruptions and changes, especially when combined, can lead to critical data loss. Therefore, backup and having a data recovery plan have become more important than ever before.
Since the start of the coronavirus pandemic, Kotar Data Recovery has been helping many individuals and businesses to restore their critical data and continue operations as seamlessly as possible.
how to protect your data while working from home.
Take these essential steps to protect your data while working from home:
1. Backup
Backing up your data is the most important thing you need to do. Make sure it becomes your routine, so that you always have an up-to-date version of your data.
2. Check your backup
Your backup may fail due to various reasons, from interruptions during the backup process to corrupt files, to a full or broken backup drive.
Therefore, always check the data to ensure the last backup was made correctly.
3. Create a strong password
Make sure you have password protection and don’t have the same password for all devices.
Strong passwords can be hard to remember, so it could be helpful to use a password manager with encrypted password protection.
4. Update virus protection
You don't want your computer to be infected with a virus or malware. For that reason, regularly update your virus protection software for all devices you use when working from home.
Despite everything, human error is still the top cause of data loss.
In case something goes wrong and you lose data, contact Kotar Data Recovery, a data recovery specialist, to get your data back.